131 | Add to Reading ListSource URL: accuratebackground.comLanguage: English - Date: 2015-04-06 16:03:40
|
|---|
132 | Add to Reading ListSource URL: www.tapaemea.orgLanguage: English - Date: 2014-09-11 09:41:17
|
|---|
133 | Add to Reading ListSource URL: www.cnb.comLanguage: English - Date: 2014-08-06 17:57:41
|
|---|
134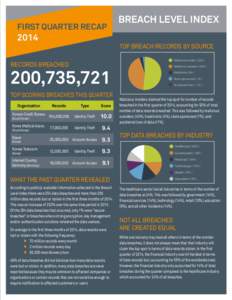 | Add to Reading ListSource URL: breachlevelindex.comLanguage: English - Date: 2016-08-03 15:31:24
|
|---|
135 | Add to Reading ListSource URL: www.cs.tau.ac.ilLanguage: English - Date: 2016-08-04 06:51:27
|
|---|
136 | Add to Reading ListSource URL: www.justaddwaterscuba.comLanguage: English - Date: 2015-12-26 07:06:10
|
|---|
137 | Add to Reading ListSource URL: cups.cs.cmu.eduLanguage: English - Date: 2005-06-21 09:58:20
|
|---|
138 | Add to Reading ListSource URL: www.arcyber.army.milLanguage: English - Date: 2016-03-15 15:31:42
|
|---|
139 | Add to Reading ListSource URL: www.usenix.orgLanguage: English - Date: 2016-02-21 12:26:57
|
|---|
140 | Add to Reading ListSource URL: cups.cs.cmu.eduLanguage: English - Date: 2007-06-22 15:47:38
|
|---|